
Last year, I remember talking to Chris Dymond and Saul Cozens just after they returned from Thinking Digital conference in Newcastle/Gateshead. They raved about how good it was. So did others I’d seen mention it online. I decided to go the following year and, as the 2016 tickets were already on sale, I booked one more or less straight away.
It was as good as I’d hoped. And so, partly to remind myself of all I learned, partly to share it with colleagues and friends, and partly to persuade you to go in 2017, here are my notes on #TDC16:
Day 1: Workshop: VR Beyond Gaming
The event kicked off with a series of short presentations from companies based at VRTGO Labs: Vector76, Secret Sauce, Hammerhead and Chronicles VR. Each company talked a little about their history and projects worked on to date, which included the Road Respect driving simulation, aimed at young drivers, 360-degree videos for Lexus and others, a full-sensory rollercoaster ride through a fridge full of food (including sounds, smells and gusts of air), and a number of projects in conjunction with museums and other attractions.
Following this, we got a chance to try out a series of simulations, games and painting programs on the HTC Vive and Oculus Rift platforms. I was particularly impressed with Google Tilt Brush, which enables you to paint around yourself in a 3D environment, but everything on the HTC Vive was a lot of fun.
Day 2: Conference
Session 1: Sport, Culture, Terrorism
Bill Jinks, CTO for Sales & Distribution at IBM
In Pursuit of Greatness
Bill talked about IBM’s 26-year partnership with Wimbledon, supplying them with the technology and expertise to make them “the best tennis tournament in the world”, and to make their cross-platform web, app and social media experience “the next best thing to being there”. There was some interesting stuff about how IBM’s focus on speed of data gathering & analysis enables them to have a faster editorial response than any media organisation covering Wimbledon, and about how they use analytics to predict demand from moment-to-moment, adjusting their web provisioning accordingly; but on the whole, the presentation was a bit too general and marketing focused.
Irini Papadimitriou, Digital Programmes Manager at the V&A
Crafting our Digital Future
Irini talked about how the Victoria & Albert Museum organises collaboration between designers, scientists, artists and technologists around different topics, harking back to the representations of Art, Science, Invention and Education on the V&A’s 19th century facade.

For example, the V&A organised a “Climate and Fashion hackathon”, in conjunction with the Met Office produced creative ideas engaging with the issue of climate change. Helen Storey’s “Dress for Our Time” was based on ideas from this hackathon.
Other recent projects include:
- “Cleaning Land for Wealth” – recovering nanometals from contaminated land.
- “Bodies of Planned Obsolescence” Work with the Restart Project on recycling and repair of electronic waste, with collaborators from the UK, China and Nigeria.
- “Money No Object” – artists exploring the future of currency & value.
- Cash donation receptacles within the museum, with decorations which psychological findings indicate may lead to greater donations (eyes taken from banknotes, looking straight at the donor; flowers; the colour red)
The V&A are holding a design festival in September, and are looking for collaborators (fields covered include architecture – so possibly some scope for Autodesk to collaborate?)
Mikko Hypponen, Chief Research Officer at F-Secure
Cyber Arms Race
Mikko described the different groups motivated to breach computer security, and how attackers’ agendas can lead to very different types of attack:
- Hackers, hobbyists and activists, wanting to make a point and perhaps shut a company down.
- Criminals, wanting to make money from cyber crime.
- Nation states, wanting to spy on, influence or destabilise another state. (NB the vast majority of security breaches perpetrated by nation states are espionage and not, as they’re often described in the press, “cyber war”).
- Terrorists, wanting to achieve political aims through whatever means necessary.
F-Secure receives 350,000 malware samples per day. 95% of these are criminal in origin.
In software, “complexity is the enemy of security”.
How many of the Fortune 500 companies are currently hacked? 500.
Most attacks spread via macro viruses (in particular, MS Office documents that prompt the user to enable editing). The biggest problem is ransomware – cyber criminals who encrypt a user’s hard disk via a Word macro, and demand payment in Bitcoin. When you pay the ransom, they will honour their promise to recover your files – after all, they have a reputation to keep up (i.e. when a user falls victim to ransomware, they will google the outcome of previous victims who paid up). This part of the presentation reminded me of the really interesting Darkode episode of Radiolab which I listened to recently.
Ransomware from 1989 looks very much like ransomware of today. But criminals target wherever they can make money – KeRanger ransomware now afflicts OS X, and will encrypt your remote Time Machine backups as well as your Mac’s disk.
Because Bitcoin records are open and viewable by anyone, it’s possible get an idea of how much money there is to make through cyber-crime: just one criminal gang made €300m in the last couple of years (tax-free, naturally).
Much (but not all) cyber-crime comes from Russia and former Eastern-block contries. This is because people there have the technical skills, but not the employment opportunities to make use of them, i.e. it is a societal problem, not a technical one.
IoT (Internet of Things) and ICS (Industrial Control Systems) are a new potential vector for attacks. Unprotected pages allowing control of many such systems can be found just by scanning IP addresses — allowing control over motors, generators, swimming pools (including turning on the “ACID PUMP”!), and even hospital beds.
Russian spies used MS Office macros sent via email to infect and take over computers in a power station run by Ukranian power company Prykarpattyaoblenergo. As a result, the Russian government was able to shut down power to large parts of Ukraine (a rare example of actual Cyberwar).
Cyber terrorism is a major future threat. The USA take this so seriously that they have assassinated hackers in Syria using drone strikes.
Session 2: Blockchains & Bassdrums
John Thorp, President at The Thorp Network
Realizing Value in a Digital World
John Thorp gave us the long view, from his perspective of having worked over 50 years in the technology industry. Despite all this time, there is a leadership deficit in the industry, with many still not “thinking digitally” but instead applying outdated approaches rooted in the industrial age. Technology needs to be viewed in the context of BTOPP: Business, Technology, Organization, Process and People.
The pace of change, and the unpredictability of emergent behaviour, means that We need a bottom-up approach, enabled and steered by good governance, i.e. continually asking “Where am I? Where am I headed? Why am I not on course? Can I plot a different course?”
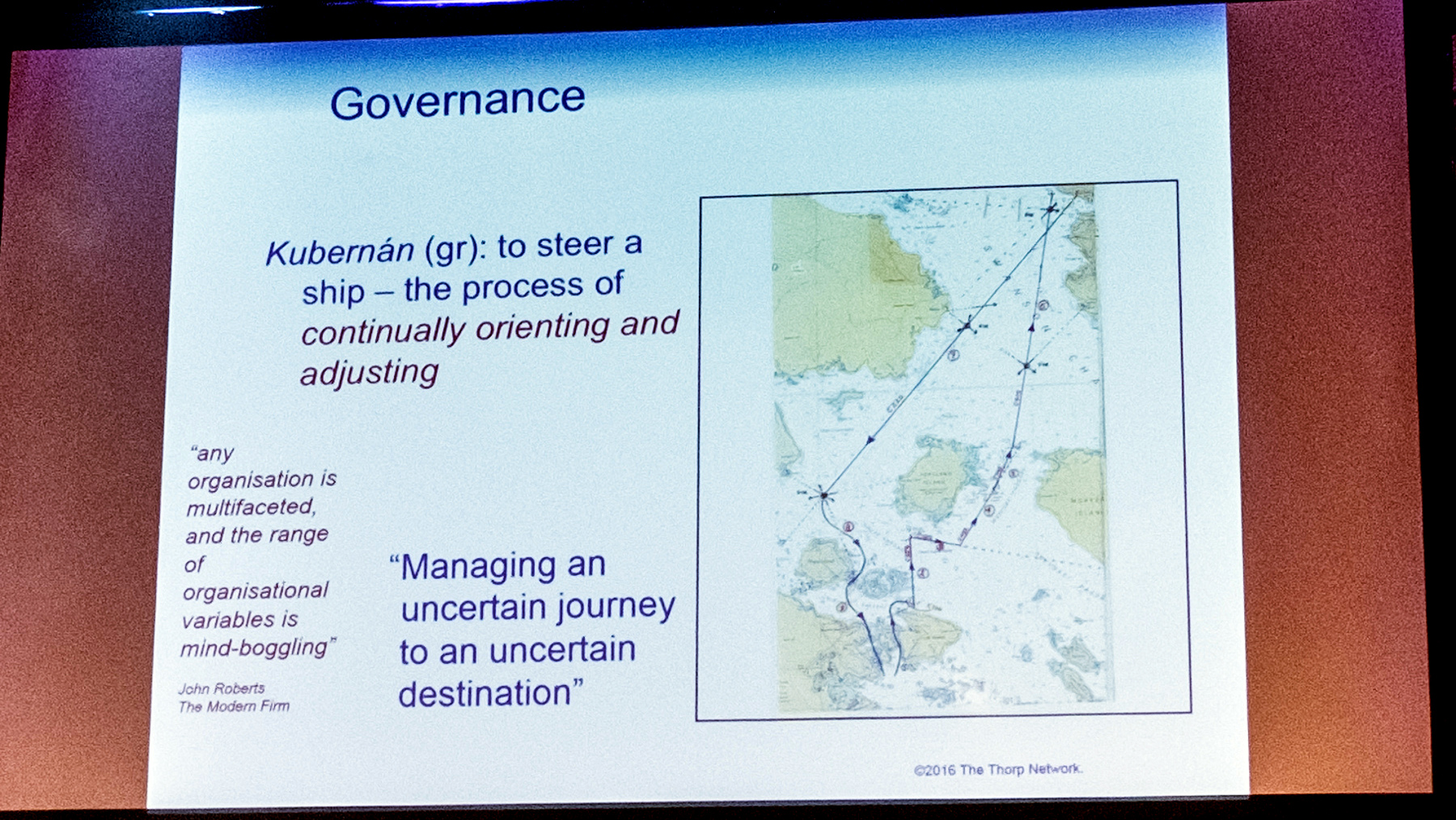
We need to move from big organisations with rigid and hierarchical infrastructure to multiple, smaller, agile organisations collaborating with one another (in my mind, I pictured this as “the company as a microservice”). The people within the organisation, those who are actually doing the work, often have the right answers, but internal politics and the self-serving nature of leadership often stifles their opinion.
Leadership is broken. We are picking the wrong leaders, because we are using old (and self-reinforcing) criteria. Our leaders often frame new techologies in terms of existing ones (e.g. First World War military leaders who said “we need those motor cars, so we can get our horses to the front quicker!”).
There was some interesting discussion after the talk around whether this might also be the same in politics – we keep getting the wrong leaders, because we are still judging by old, industrial-age criteria.
Sarah Meiklejohn, Computer Science Lecturer at University College London
Clearing the path for Transparent Technologies
Sarah talked about blockchains, but focused more on the why than the what: Not “what is a blockchain?” but “why use a blockchain?”

Many systems require one or more intermediaries – data gateways or interfaces – in whom we place our trust. We trust our banks, communications platforms, and cloud storage to provide confidentiality. We assume that various trustmarks guarantee integrity. Yet we cannot be certain how these intermediaries operate, and to what extent we should really place our trust in them.
For example, when we are online, the padlock in the browser bar is a guarantee that the page is encrypted, and our commnications secure. But who is involved in making it secure? The SSL certificate could be issued by, for example, Comodo, GlobalSign, DigiCert, or Trustwave; the communication could be taking place across networks operated by Tata, Pacnet, Level 3, or Hibernia; and the encryption mechanism could be backed by NIST, ITU-T, NSA or ETSI.

By making the intermediate processes more transparent, and opening them up to scrutiny, we can better understand where we are placing our trust.

Another example of intermediaries in the music industry. Consumers of music (Spotify, radio stations, film-makers, etc) use an intermediary (PRS, BMI, …) to identify and recompense creators of music. Blockchain technology could takes the place of that intermediary, replacing the opaque silo with a distributed, open ledger.
Ed Hipkins – Bassdrummer

Ed played drums and drum-triggered synthesizers to make dance music. In between doing so he talked about how recognising limitations, working within them and looking for novel ways around them engenders creativity. As well as his own limitations (his skills as a drummer, and the number of pads he has available), he talked about how the restrictive factors have influenced piano music – with Mozart using the new instrument to move beyond the uniform notes of the harpsichord, and then John Cage taking things further with prepared piano.
Session 3: The Searchers
Will Dracup, CEO at Bio Signatures
Sub-prime Science
Will was talking about the difficulties of scientific research. He spoke with particular reference to his field: proteomics, the analysis of different proteins in the blood of healthy people and people with particular illnesses, and determining the difference.
He mentioned several times “the problem with science” but, as far as I could work out, didn’t state what this problem is. A symptom of it is that newspapers print articles saying “a glass of wine a day prevents of cancer” and then, a few weeks later, printing that “a glass of wine a day causes cancer”. And the solution to the problem apparently involved blind trials. What the problem is though, I’m not sure.
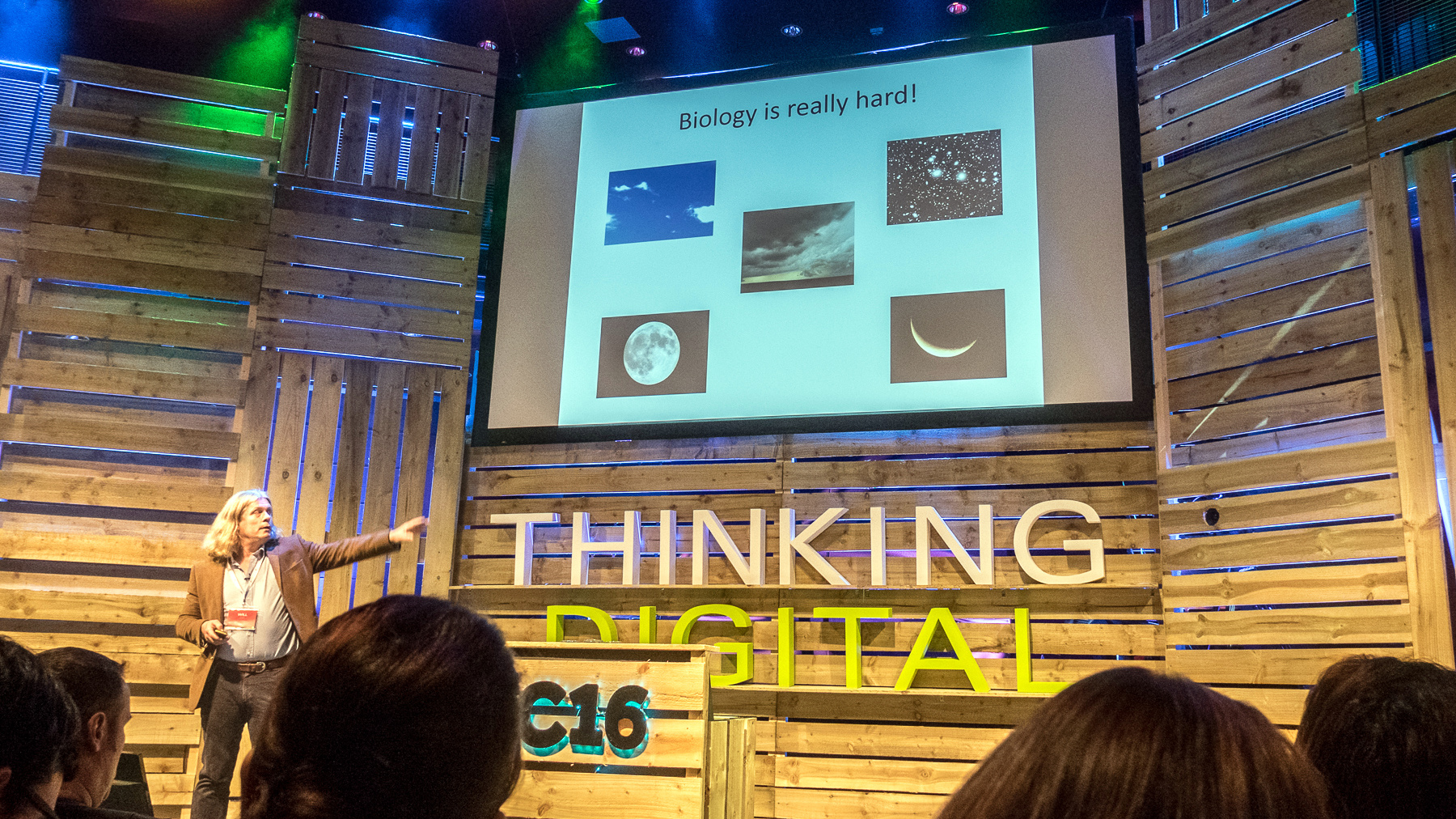
One analogy Will used to contextualise biology research, which I particularly liked, was looking for the moon by scrutinising a tiny section of the sky: you may have a theory that there is a round object in the sky called the moon, but you might take thousands of samples of your small part of the sky without ever seeing anything round that conforms to your expected image of the moon. In biological research, with thousands of factors in play, the chance of spotting your “moon” through your impossibly tiny “window” is even narrower.
James Murray, Search Advertising Lead at Microsoft
Decoding Human Context
James gave a fascinating talk on how Microsoft Bing is taking into account the context in which search takes place, rather than just the words used to frame a search. Searching for “Paris Hilton” can mean that you’re looking for somewhere to stay in France, or that you’re interested in socialite heiresses. When we search, we don’t always event want what we ask for: anyone searching for “Jurassic Park release date” last year was probably actually more interested in the release date of Jurassic World (June 2015) than in the July 1993 movie.
Of course, Bing is the underdog in the field of search, with Google owning not just the market share, but also the verb “to google”. However by building context-aware search Microsoft hopes that, just as almost everyone in the audience hoovers with a Dyson, one day everyone will google with Bing.
There are four types of context which Bing uses or intends to use:
- Emotional: e.g. using facial expression tracking to figure out how the user feels. This has been a long time coming – I remember in 1996 reading Being Digital by Nicholas Negroponte and being very excited at the prospect of emotion monitoring and eye-tracking, so that, for example, a computer can tell when you’re getting pissed off with it, and adapt its approach accordingly, rather than just spewing out the same response over and over.
- Environmental: e.g. Bing might figure out your preferences, and if you ask for a coffee then it would find your favourite type of coffee shop close by, rather than just any old coffee shop. But if the weather is bad, then it might instead find you the nearest coffee shop, even when it’s not your favourite.
- Social: e.g. Kinect can tell who you are watching TV with, and even whether those other people are actually watching or are doing something else, like fiddling with their phone. Based on this information, Netflix could make different movie recommendations to you depending on whether you are watching alone, with a partner, or with kids.
- External: based on your culture and personal history, what you expect in a particular context will differ from what somebody else expects in that same situation. Disney was shown as an example of a company that tailors its movies to each country they are shown in.
Some interesting asides included how Microsoft Research in Cambridge use employees’ faces as their security badges; the same system also updates their calendar, showing when they are in the office, and will automatically call a lift and route it to the correct floor on their arrival. I couldn’t help but think how I would try to game this, adjusting my beard regularly, maybe experimenting with make-up, and formulating a dazzle-ships-type strategy for preventing facial recognition.
As a lead-in to the new Skype live translator, James showed how he embarassed himself when giving a speech at his wedding, his slightly-off Mandarin intonation hilariously altering the meaning of a crucial sentence:

In conclusion, James said that content is not king, context is.
Tom Scott, @tomscott
Accidental Emoji Expert
Tom developed emoj.li, an emoji-only instant messaging service (“we didn’t think we would have to add a profanity filter, but we did. SO many aubergines.”). This took me back to 2000 when my colleague, the amazing Steve ‘moo-moo’ Williams, developed a set of visual icons called Chewchat for Kellogg’s Real Fruit Winders, something which was intended to allow kids to develop their own secret languages, communicating only in pictures, and which for me was a clear forerunner to emoji.
Tom talked about the crazy history of emoji, from obscure origins in Japan, via a last-minute space-filler for unused slots in Unicode, to becoming a major responsibility (and major headache) of the Unicode consortium, and something so ubiquitous that you can now buy emoji cushions in tat-stores. He also talked about his own involvement, including developing an emoji keyboard — or rather, series of keyboards — which, rather bizarrely, he had to demonstrate on BBC Radio 2.

He also talked about new emoji proposed for 2016 and 2017, including new modifiers (left-facing vs. right-facing, male vs. female vs. non-specific gender) and a new condom emoji which should make an interesting way for young people to communicate about safe sex.
Session 4: Present at the Creation
Joe Faith, Product Manager at Google
Product Development at Google
Joe talked about the Google’s process for developing new products:
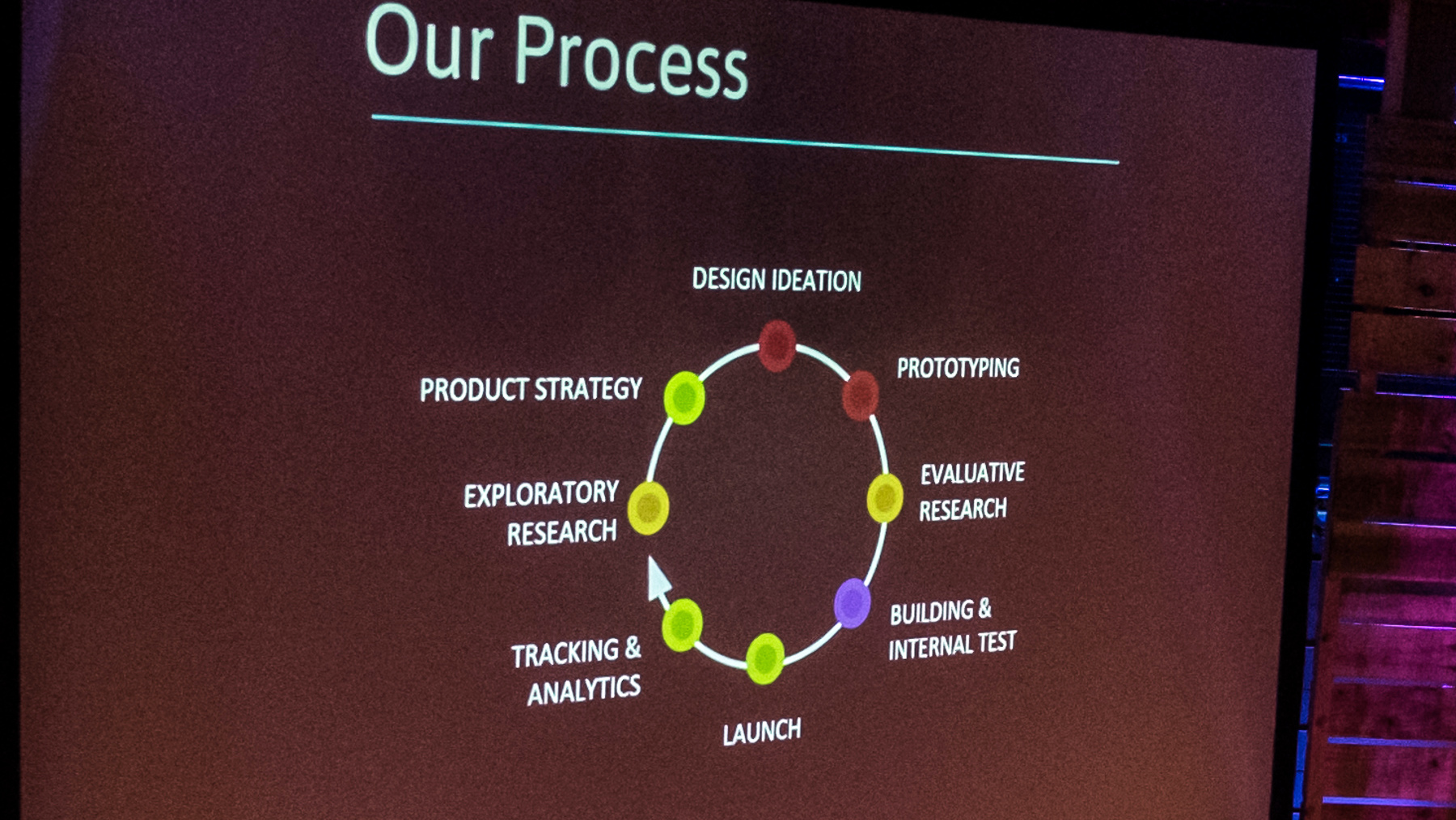
And about the reality of developing new products at Google:
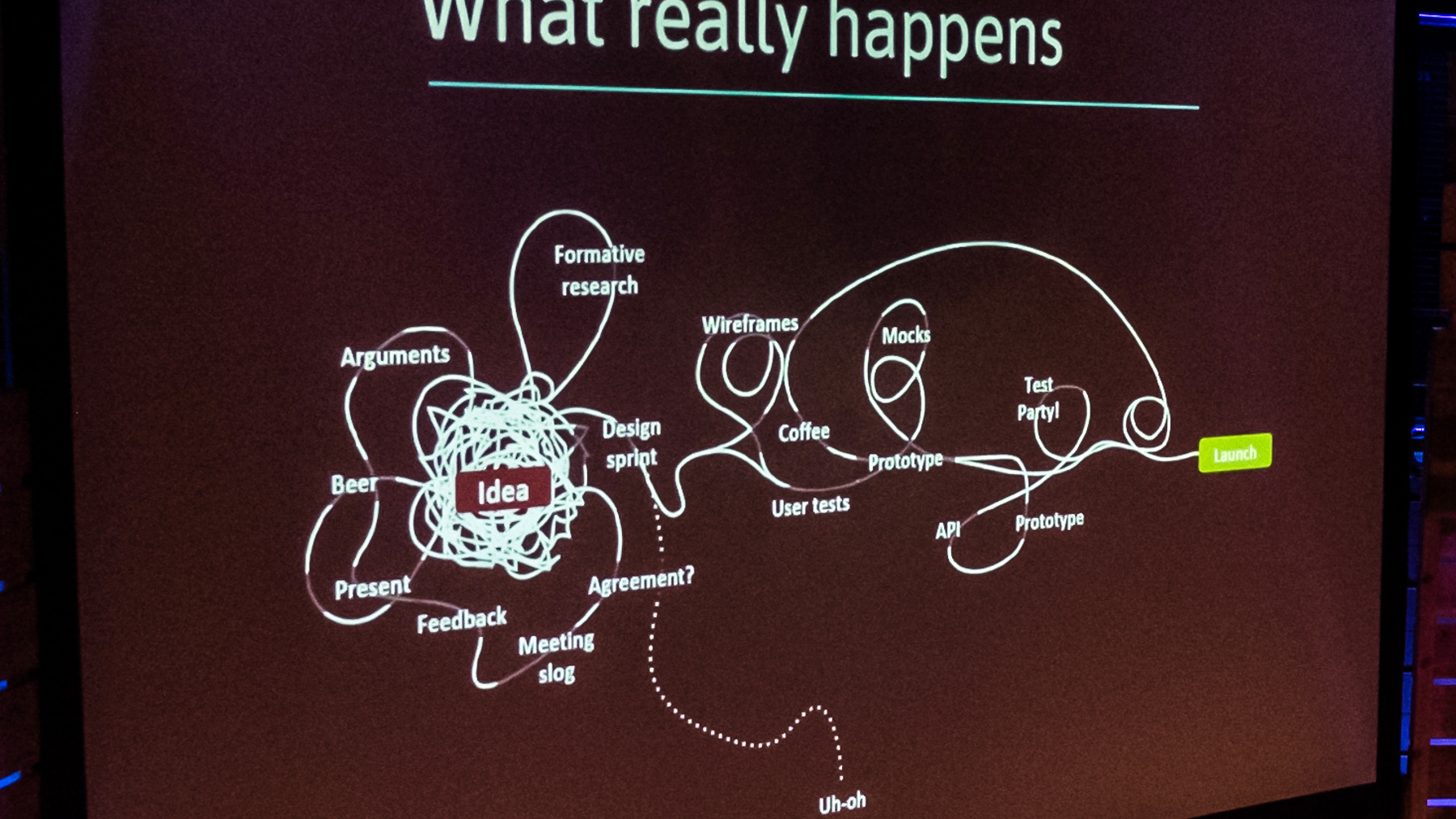
He said that, because of the DNA of its people, Google is “the least process-driven of any large company that I know”. However, they do follow some principles:
1: Focus on the user
Google’s focus is on adoption, not on monetization. Focus on the user and, if you get it right, the money will follow. So, for example, Android is given away for free; the Play Store is now a big earner for Google, but it was not even conceived of when they started giving Android away.
He also talked about ideas providing the opportunity to pivot, such as when Amazon turned the need to build huge network capacity for the Christmas shopping rush — capacity which Amazon does not need the rest of the year — into its AWS cloud platform and, in so doing, launched an entirely new industry.
2: What’s the 10x
In what way does a new product provide something ten times better than what already exists? A two-times multiplier is not worth building — in most cases you could manage a 2x improvement just by tweaking current conditions. And a 100x improvement is in the realms of science-fiction. But 10x is both achievable and worthwhile.
It doesn’t have to be ten times better at everything: just one area in which your product is clearly better than anything else out there gives you enough to build on. For example, when Google Docs launched, it had very few features compared with traditional word processors and spreadsheets. But what it had was cloud storage and collaborative editing, which meant no more having to trawl interminable folders for “Document-final-edit-v3-revised.doc”.
Working in this 10x space means that you are always working on problems somewhere outside your comfort zone (as Joe said, Google isn’t all free sushi and nap-pods… although it is those things too).
3: Launch and iterate
Launch early to find problems. Fix those problems. Iterate, and keep iterating to make the product better.
When Google Chrome launched (internally, to just a few engineers at Google) it could not even display a web page. There was no HTML renderer in Chrome. All it was was an update mechanism: one of two “10x” benefits which Chrome bought was the ability to update automatically, without the need for the user to manually download new software and restart (the other 10x benefit was Chrome’s speed). So the first ever Chrome was just a box on a screen which automatically updated when the next version of Chrome (which, presumably, could display at least the most basic of web pages) was released.
Points 1, 2 and 3 above form a Minimum Viable Product: user focused, with a 10x benefit, and the ability to iterate fast.
Katherine Courage – Journalist & Author, contributing editor for Scientific American magazine
Cultured: The Mighty Microbiome
Katherine talked to us about the Microbiome – the trillions of organisms which form an incredible ecosystem inside the gut of every one of us. I’d learned a little about this hidden world reading Gulp by Mary Roach, and it’s a fascinating one.
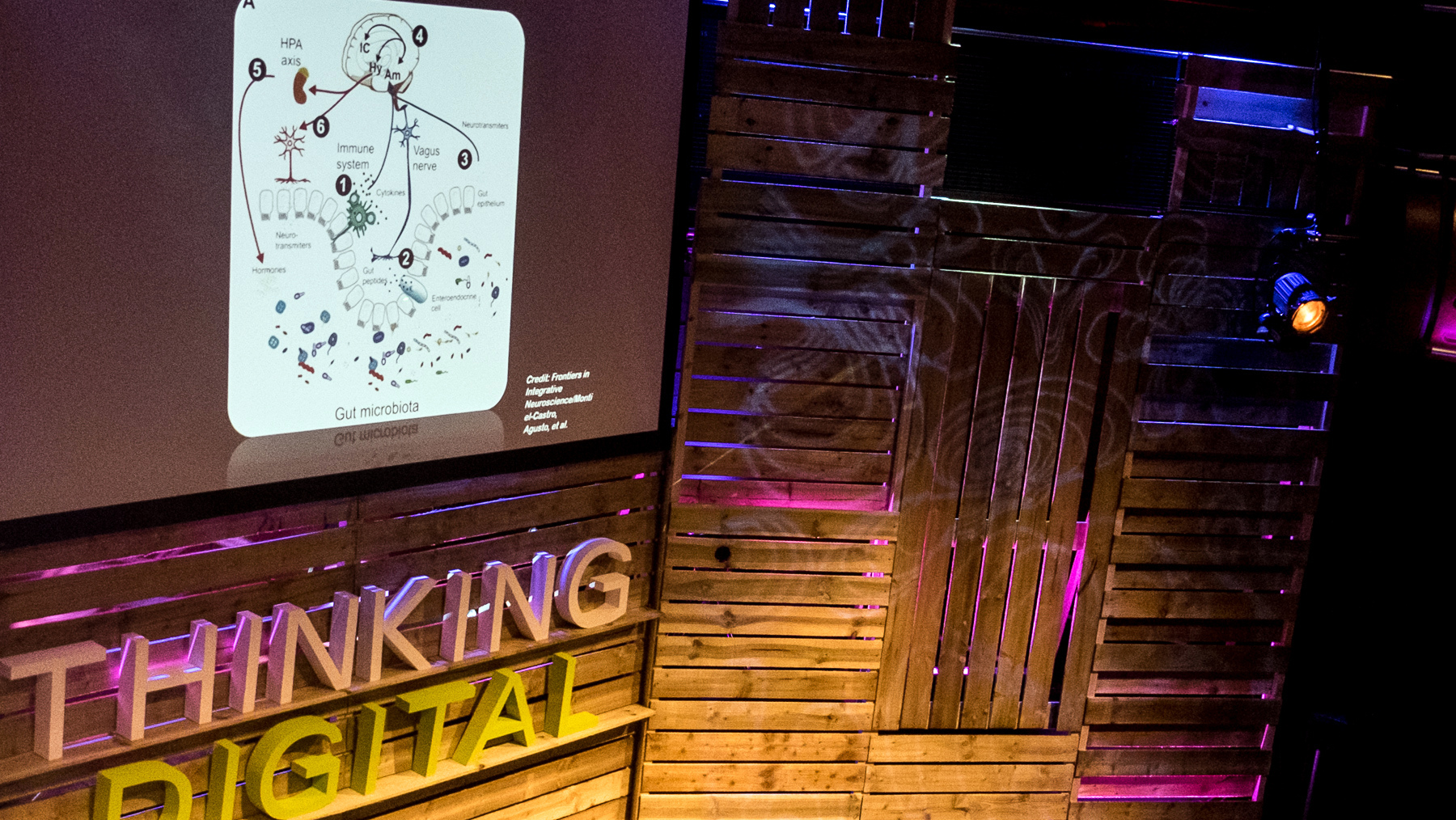
The gut has close connections with the nervous system and, via it, the brain, and there is increasing evidence that the makeup of microbia inside us has a huge effect on our physical and even our mental health.

I’m happy to say that Katherine talked a little about FMT – that’s poo transplants to you and me. I was interested to learn that there are companies now which, like 23-and-me for poo, will analyse the contents of your gut for you and show how you differ to others. In a bold step for the lifetracking movement and the quantified self, we may even soon have turd-analysing toilets which measure changes in your gut flora from day to day, to warn you when your crap is crap. Things really have moved on since the days of ratemypoo.com!
Katherine also talked about yoghurt, kimchi, and other live cultures, and how they may help re-culture the microbiome (provided they’re eaten often).
MT Rainey OBE – Deputy Chair at Channel 4
MT gave the closing speech of the conference, and although she professed to be not a very digital-savvy person (in her early days in advertising, when her company helped to launch Lil-Lets, the term “digital” was used in the feminine hygiene industry to refer to tampons) she was present at some fascinating events.
As a 23 year-old junior ad exec at Chiat Day, she was assigned to one of their smaller clients, a computer company called Apple. She talked about filming ads for the Apple Lisa in 1983, with Ridley Scott and the similarly novice Kevin Costner (and his dog). And about helping Steve Jobs take on the board of Apple, persuading them to allow a single screening of the advert they’d put so much into (filmed at Shepperton Studios, where in 1985 I started work at my Uncle’s company), a masterpiece which eventually became history.
MT shared many more memories of her times working and socialising with Steve Jobs, about the parts Danny Boyle’s recent movie got right, and those it didn’t. She painted a picture of an unconventional perfectionist, who didn’t care what others thought of him, but who could care deeply about others, and was a champion of sexual and racial equality (not so much for equality’s sake, but simply because by shutting out huge sections of the population you are letting so much talent go to waste).
She also showed some old videos of Marshall McLuhan, incredible stuff featuring his predictions about the Internet and Social Media many years before the event.
And then…
Finally, we wrapped up, and headed across the river for the closing party at Eye on the Tyne. There, after almost ten-years of Twitter followdom, I finally got to hang out with the lovely Christian Payne AKA Documentally.

I should also mention the organiser and host of Thinking Digital, Herb Kim. I had met Herb before — he spoke at the Interesting North conference which I helped to organise in Sheffield back in 2011 (well, “organise;” rather overstates my role, but I did attend the planning meetings and conversations on Google Wave, and I took photos of the day including some of Herb), and since then we’ve chatted occasionally on social media and at TEDxHousesOfParliament which Herb also runs. But this was the first time I’d seen him in full-on host mode, and it was quite something.
Of course, Herb did a great job setting the scene for each speaker, and he also asked some interesting and pertinent questions to each after they had spoken, which really enhanced the talks. But two things really stood out, compared to most other conferences I’ve been to. First, how smoothly Herb incorporated the sponsors into the event, bringing them up on stage, telling us their story and how they fit in with Thinking Digital. And second, the subtle, low-key way with which he presented; he made it look effortless, which I presume indicates that it was anything but.

Just one more thing: there were some spectacular videos shown in between the sessions.This one in particular moved me greatly, so I wanted to share it.
(This post originally appeared on A Life Less Literary – many thanks to Dan for letting us republish it!)